Reverse Engineering Puzzles #1 - stack frame and local variables
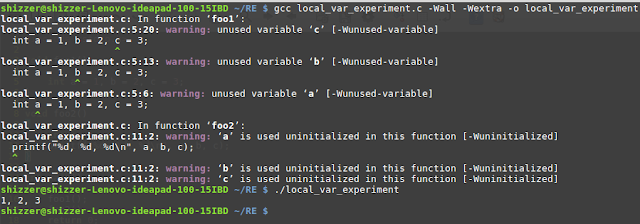
Hello everyone While doing some experiments with C language I thought that it will be fine to share the interesting results with you. And this is what this new series is all about - when I find something curious I am going to write about it on my blog. Today's topic is the deeper look at the stack frame .