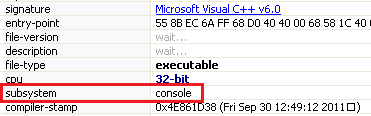
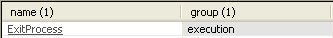
Hello everyone! This time I'm gonna show you how I've solved tasks from the Basic Dynamic Analysis chapter. Obviously, these labs are provided by "Practical Malware Analysis" book written by Michael Sikorski and Andrew Honig. Basic dynamic analysis is a good second step in the whole process of researching malware. Basic dynamic analysis techniques can confirm the supposition of what malicious program really does. Of course, this type of examining malware isn't enough to get the whole knowledge about the structure of a malware. I'll describe more techniques as the book advances. Now I invite you to read my solutions and I hope that you'll learn something with me. :) Tools that I use in basic dynamic analysis: Process Monitor, Process Explorer, Regshot, ApateDNS, INetSim, Wireshark. I described them here -> https://shizz3r.blogspot.com/2020/06/beginning-of-malware-analysis-adventure_19.html