Learning of malware analysis. Basic dynamic analysis labs from "Practical Malware Analysis" book
Hello everyone!
This time I'm gonna show you how I've solved tasks from the Basic Dynamic Analysis chapter. Obviously, these labs are provided by "Practical Malware Analysis" book written by Michael Sikorski and Andrew Honig. Basic dynamic analysis is a good second step in the whole process of researching malware. Basic dynamic analysis techniques can confirm the supposition of what malicious program really does. Of course, this type of examining malware isn't enough to get the whole knowledge about the structure of a malware. I'll describe more techniques as the book advances. Now I invite you to read my solutions and I hope that you'll learn something with me. :)
Tools that I use in basic dynamic analysis: Process Monitor, Process Explorer, Regshot, ApateDNS, INetSim, Wireshark. I described them here -> https://shizz3r.blogspot.com/2020/06/beginning-of-malware-analysis-adventure_19.html
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Lab 3-1
Analyze the malware found in the file Lab03-01.exe using basic dynamic analysis tools.
Questions:
1. What are this malware’s imports and strings?
2. What are the malware’s host-based indicators?
3. Are there any useful network-based signatures for this malware? If so, what are they?
My answers:
1) What are this malware's imports and strings?
The best tool in my arsenal to examine imports and strings is pestudio which I was using while basic static analysis. The result of checking Lab03-01.exe by pestudio is as follows:
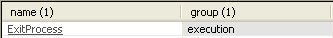
Imports:
Strings:
As you can see the number of imports is very suspicious. It's not possible for the unpacked file to have so few imported functions. There is only one method called ExitProcess and this is a very strong indicator that the file is packed. It looks like strings aren't packed since there are exactly 43 strings within the executable.
In my opinion, the most important strings are these ones:
- CONNECT %s:%i HTTP/1.0\r\n\r\n
- www.practicalmalwareanalysis.com
- admin
- vmx32to64.exe
- SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- advpack
- VideoDriver
- WinVMX32-
2) What are the malware’s host-based indicators?
We can find host-based indicators with greater accuracy using basic dynamic analysis techniques. This time we are able to observe new processes created on runtime and called syscalls as well as their results. So let's find some malware's host-based indicators. First of all, we have to run all-important tools which will be helpful in the case of finding malware's host-based and network-based indicators by occasion.
1. Run the Process Monitor to get an overview of called syscalls within the analyzed process. Obviously, it's a must to set appropriate filters since we would have been confused with lots of unnecessary syscalls from all over the system. In addition Process Monitor capture syscalls from most of the processes running on the system and saves them into RAM. Therefore it's important to disable capturing events before running the suspected program and after it when we decide to stop.
2. Launch the Process Explorer to check if analyzed program creating and run new processes. If so, then we have to analyze them later on.
3. Taking a first snapshot of the registry using Regshot and compare it with the second snapshot after running the malware. This would give us a clear overview of changes within the registry.
After setting up a filter in Process Monitor to Process Name is Lab03-01.exe I've got a list of called syscalls by this exact process. Here they are:
Obviously, this is only a part of the whole list because Process Monitor captured exactly 686 syscalls called by the executable. In this question, we are focused on host-based indicators of analyzed malware, therefore, we can apply Show File System Activity filter and disable the rest of filters.
Now the number of syscalls decreased from 686 to 356. From this list of called functions, I can tell that a lot of them are used for loading DLLs since I've found only one import before. The best operation to look for when someone wants to find host-based indicators is CreateFile function I think. "Operation is CreateFile" filter did the job for me. In a moment I had the list of all CreateFile syscalls called by the process along with its arguments and results.
I've decided to avoid every call to CreateFile in case of .dll since all of these calls had been done for loading libraries into the memory of the process. It's worth looking at two operations with vmx32to64.exe. Lab03-01.exe creates a new suspected file for sure so vmx32to64.exe is malware's host-based indicator indeed. I was curious about what this file really is so I looked at every file-system operation done with vmx32to64.exe.
Unfortunately, this screen isn't visible enough to gain information but I can tell that in the first red rectangle there is Offset: 0, Length: 7,168 and the called function is ReadFile done on Lab03-01.exe. In the second red rectangle, there is WriteFile operation done on vmx32to64.exe and the information provided by Process Monitor is again Offset: 0, Length: 7,168. This probably means that Lab03-01.exe copies itself to vmx32to64.exe. I confirmed it by checking SHA1 hashes of the vmx32to64.exe and Lab03-01.exe files.
SHA1 hashes of these two files are equal so now it's clear that Lab03-01.exe copies itself into vmx32to64.exe indeed. After checking file-system syscalls the time came for taking a look at registry changes done by the malware. There was no need to exit the Process Monitor tool and one thing to do was to simply change the filter to Show registry activity. The case was to find host-based indicators so I'd added another filter option -> Operation is RegSetValue which has allowed me to investigate registry writes done by the suspected program.
Without any doubt, the most important information is the marked one. The malware has written VideoDriver key into Run within the registry.
Regshot has also given this information to me. Then I've checked the whole write into Run using Regedit to find if the path written in Run/VideoDriver is the path to Lab03-01.exe or vmx32to64.exe actually.
Of course, the path was set to vmx32to64.exe which means that the malware executes each time the system is booting.
I've written about DLLs loaded by the malware, therefore, it's worth to check if I was right. To get information about loaded DLLs I've used Process Explorer and View -> Lower Pane -> DLLs option.
The above picture shows the whole list of loaded DLLs by the process so I was thinking right. Another interesting feature of the Process Explorer tool is checking for Handles of the analyzed program. To find them let's use View -> Lower Pane -> Handles.
The most significant part of the list of opened handles by Lab03-01.exe is Mutant in my opinion. WinVMX32 file is used by the malware probably to check if the system is already infected and if it is then malware doesn't infect OS again. So WinVMX32 is another malware's host-based indicator.
Summary:
malware's host-based indicators are:
- vmx32to64.exe in C:\Windows\system32
- VideoDriver key within the Run folder of the registry and the path sets to C:\Windows\system32\vmx32to64.exe
- WinVMX32 as the Mutant
3) Are there any useful network-based signatures for this malware? If so, what are they?
I've decided to first investigate any called syscalls done by the executable using the Process Monitor tool. To my surprise, there were no syscalls responsible for networking.
To be able to check for useful network-based signature for the malware we should use appropriate tools such as INetSim, ApateDNS, and Wireshark.
1. Launch Linux fake network machine and then run INetSim to be able to take requests from malware
2. Run Wireshark on Windows machine to capture packets that will be sent by the malicious program.
3. Use ApateDNS and set the DNS redirection within this tool to the IP address of Linux machine. It has to be done because malware has to send requests only within our fake network and not spread across a real network.
The result from ApateDNS:
The malware tries to connect to the www.practicalmalwareanalysis.com. So this domain is the network-based signature for Lab03-01.exe.
Captured packets by Wireshark:
Obviously, the list is much bigger but the important thing is that in this bunch of captured packets we have TCP protocol. Now the communication between malware and an exemplary host can be read by us. Wireshark has a very useful method to get through TCP packets called Follow TCP stream. This is the result of this feature:
These are the bytes from the communication between malware and the host. The whole data is probably encrypted. The port of the outbound connection from the Windows machine is 443 which means that the malware tries to communicate with the other host through the HTTPS protocol.
To confirm or reject this supposition I've run the test with the same tools several times. The data sent by the malware through port 443 was random each time which means that the malware doesn't communicate with another host using HTTPS protocol. If we want to understand this communication we would have to do reverse engineering of the binary and as a result of this reverse engineering of the protocol itself.
Summary:
network-based signatures of the malware are:
- connections to the domain: practicalmalwareanalysis.com
- communication using "random" data between the malware and domain through the port 443
Analyze the malware found in the file Lab03-01.exe using basic dynamic analysis tools.
Questions:
1. What are this malware’s imports and strings?
2. What are the malware’s host-based indicators?
3. Are there any useful network-based signatures for this malware? If so, what are they?
My answers:
1) What are this malware's imports and strings?
The best tool in my arsenal to examine imports and strings is pestudio which I was using while basic static analysis. The result of checking Lab03-01.exe by pestudio is as follows:
Imports:
Strings:
As you can see the number of imports is very suspicious. It's not possible for the unpacked file to have so few imported functions. There is only one method called ExitProcess and this is a very strong indicator that the file is packed. It looks like strings aren't packed since there are exactly 43 strings within the executable.
In my opinion, the most important strings are these ones:
- CONNECT %s:%i HTTP/1.0\r\n\r\n
- www.practicalmalwareanalysis.com
- admin
- vmx32to64.exe
- SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- advpack
- VideoDriver
- WinVMX32-
2) What are the malware’s host-based indicators?
We can find host-based indicators with greater accuracy using basic dynamic analysis techniques. This time we are able to observe new processes created on runtime and called syscalls as well as their results. So let's find some malware's host-based indicators. First of all, we have to run all-important tools which will be helpful in the case of finding malware's host-based and network-based indicators by occasion.
1. Run the Process Monitor to get an overview of called syscalls within the analyzed process. Obviously, it's a must to set appropriate filters since we would have been confused with lots of unnecessary syscalls from all over the system. In addition Process Monitor capture syscalls from most of the processes running on the system and saves them into RAM. Therefore it's important to disable capturing events before running the suspected program and after it when we decide to stop.
2. Launch the Process Explorer to check if analyzed program creating and run new processes. If so, then we have to analyze them later on.
3. Taking a first snapshot of the registry using Regshot and compare it with the second snapshot after running the malware. This would give us a clear overview of changes within the registry.
After setting up a filter in Process Monitor to Process Name is Lab03-01.exe I've got a list of called syscalls by this exact process. Here they are:
Obviously, this is only a part of the whole list because Process Monitor captured exactly 686 syscalls called by the executable. In this question, we are focused on host-based indicators of analyzed malware, therefore, we can apply Show File System Activity filter and disable the rest of filters.
Now the number of syscalls decreased from 686 to 356. From this list of called functions, I can tell that a lot of them are used for loading DLLs since I've found only one import before. The best operation to look for when someone wants to find host-based indicators is CreateFile function I think. "Operation is CreateFile" filter did the job for me. In a moment I had the list of all CreateFile syscalls called by the process along with its arguments and results.
I've decided to avoid every call to CreateFile in case of .dll since all of these calls had been done for loading libraries into the memory of the process. It's worth looking at two operations with vmx32to64.exe. Lab03-01.exe creates a new suspected file for sure so vmx32to64.exe is malware's host-based indicator indeed. I was curious about what this file really is so I looked at every file-system operation done with vmx32to64.exe.
Unfortunately, this screen isn't visible enough to gain information but I can tell that in the first red rectangle there is Offset: 0, Length: 7,168 and the called function is ReadFile done on Lab03-01.exe. In the second red rectangle, there is WriteFile operation done on vmx32to64.exe and the information provided by Process Monitor is again Offset: 0, Length: 7,168. This probably means that Lab03-01.exe copies itself to vmx32to64.exe. I confirmed it by checking SHA1 hashes of the vmx32to64.exe and Lab03-01.exe files.
SHA1 hashes of these two files are equal so now it's clear that Lab03-01.exe copies itself into vmx32to64.exe indeed. After checking file-system syscalls the time came for taking a look at registry changes done by the malware. There was no need to exit the Process Monitor tool and one thing to do was to simply change the filter to Show registry activity. The case was to find host-based indicators so I'd added another filter option -> Operation is RegSetValue which has allowed me to investigate registry writes done by the suspected program.
Without any doubt, the most important information is the marked one. The malware has written VideoDriver key into Run within the registry.
Regshot has also given this information to me. Then I've checked the whole write into Run using Regedit to find if the path written in Run/VideoDriver is the path to Lab03-01.exe or vmx32to64.exe actually.
I've written about DLLs loaded by the malware, therefore, it's worth to check if I was right. To get information about loaded DLLs I've used Process Explorer and View -> Lower Pane -> DLLs option.
The above picture shows the whole list of loaded DLLs by the process so I was thinking right. Another interesting feature of the Process Explorer tool is checking for Handles of the analyzed program. To find them let's use View -> Lower Pane -> Handles.
The most significant part of the list of opened handles by Lab03-01.exe is Mutant in my opinion. WinVMX32 file is used by the malware probably to check if the system is already infected and if it is then malware doesn't infect OS again. So WinVMX32 is another malware's host-based indicator.
Summary:
malware's host-based indicators are:
- vmx32to64.exe in C:\Windows\system32
- VideoDriver key within the Run folder of the registry and the path sets to C:\Windows\system32\vmx32to64.exe
- WinVMX32 as the Mutant
3) Are there any useful network-based signatures for this malware? If so, what are they?
I've decided to first investigate any called syscalls done by the executable using the Process Monitor tool. To my surprise, there were no syscalls responsible for networking.
To be able to check for useful network-based signature for the malware we should use appropriate tools such as INetSim, ApateDNS, and Wireshark.
1. Launch Linux fake network machine and then run INetSim to be able to take requests from malware
2. Run Wireshark on Windows machine to capture packets that will be sent by the malicious program.
3. Use ApateDNS and set the DNS redirection within this tool to the IP address of Linux machine. It has to be done because malware has to send requests only within our fake network and not spread across a real network.
The result from ApateDNS:
The malware tries to connect to the www.practicalmalwareanalysis.com. So this domain is the network-based signature for Lab03-01.exe.
Captured packets by Wireshark:
Obviously, the list is much bigger but the important thing is that in this bunch of captured packets we have TCP protocol. Now the communication between malware and an exemplary host can be read by us. Wireshark has a very useful method to get through TCP packets called Follow TCP stream. This is the result of this feature:
These are the bytes from the communication between malware and the host. The whole data is probably encrypted. The port of the outbound connection from the Windows machine is 443 which means that the malware tries to communicate with the other host through the HTTPS protocol.
To confirm or reject this supposition I've run the test with the same tools several times. The data sent by the malware through port 443 was random each time which means that the malware doesn't communicate with another host using HTTPS protocol. If we want to understand this communication we would have to do reverse engineering of the binary and as a result of this reverse engineering of the protocol itself.
Summary:
network-based signatures of the malware are:
- connections to the domain: practicalmalwareanalysis.com
- communication using "random" data between the malware and domain through the port 443
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Lab 3-2
Analyze the malware found in the file Lab03-02.dll using basic dynamic analysis tools.
Questions:
1. How can you get this malware to install itself?
2. How would you get this malware to run after installation?
3. How can you find the process under which this malware is running?
4. Which filters could you set in order to use procmon to glean information?
5. What are the malware’s host-based indicators?
6. Are there any useful network-based signatures for this malware?
My answers:
1) How can you get this malware to install itself?
This malware is the DLL file so we have to run it manually since OS doesn't know how to launch it automatically. rundll32.exe was created to run DLLs and I'm going to use it to be able to do basic dynamic analysis on Lab03-02.dll file. The executable which can run DLL files actually only calls the indicated method within a DLL. Therefore when we want to install this malware we have to find the appropriate function to call. I'll use pestudio to examine Exports of the Lab03-02.dll file.
Exports:
ServiceMain and UninstallService functions indicate that this kind of malware is a service. To confirm this supposition we can look for imports and check if this dll uses other methods responsible for handle services.
And the Import Table gives us very interesting information:
Methods marked with a red rectangle are responsible for handle services indeed. Now we are sure that Lab03-02.dll installs itself as a service. Within a blue rectangle, there are functions that are here probably due to saving a service into the registry. Orange rectangle marked methods that indicate the behavior of the malware. Lab03-02.dll probably delivers the next module of the malware through HTTP protocol and this DLL might be a downloader.
So now when we know that the service is probably saved within the registry we might be able to get the name of this service from the registry and then run it.
Before installation, it's worth launching several tools to get as much information as possible from our basic dynamic analysis.
1. Run Process Explorer to examine processes running on the system
2. Start Wireshark to capture packets and analyze network traffic between malware and the server
3. Create a fake network using the Linux machine with INetSim and ApateDNS on the Windows machine to redirect malware into the fake HTTP server running on the Linux machine.
4. Take a snapshot of the registry using Regshot and after running malware take a second snapshot, then compare two snapshots. As a result, we will probably get the name of the service written into the registry.
To install this malware we should call Install or installA function. Let's try the first option:
There were no errors so it looks like the service is installed successfully using Install method.
2) How would you get this malware to run after installation?
After the successful installation of the service, there is probably the new key added to the registry with the name of the service. So the first thing to do is to take the second snapshot of the registry using Regshot and compare it with the first one. As a result of this, we can get the name of the service and if we have the name of the service we can basically run it.
IPRIP is probably the name of the installed service after running Lab03-02.dll. Let's confirm it by looking deeper into the information provided by Regshot. If you take a look at Values added section of the text file provided by Regshot you would see this exact line among others:
HKLM\SYSTEM\ControlSet001\Services\IPRIP\Parameters\ServiceDll: "C:\Documents and Settings\xxx\yyyy\Practical Malware AnalysisLabs\BinaryCollection\Chapter_3L\Lab03-02.dll"
Obviously in your case folders might be different but the fact is this write in the registry means that the IPRIP service is created by Lab03-02.dll indeed.
So to run this malware after installation I simply used this command:
net start "IPRIP"
What is interesting, "IPRIP" isn't the only possible name for this service. If we examine strings carefully we should see that in the bunch of trash there is something very useful for us ->
This line of characters means that the list of possible names for the service is in SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost\netsvcs registry key. If you take a look at this key you will see that the other possible names for this service are:
- 6to4
- AppMgmt
- AudioSrv
- CryptSvc
- DMServer
- DHCP
...
- and of course IPRIP
All of these names can be used to indicate the malware on infected machines. Furthermore, now we can suppose that the function installA <name to specify> can install the malware with any name from the netsvcs list.
3) How can you find the process under which this malware is running?
The best way to find the process under which this malware is running is to use Find -> Handle or DLL and type Lab03-02.dll. After doing this in Process Explorer this tool will give us the malware's process.
Now we know that the process under which this malware is running is svchost.exe with PID 1072.
4) Which filters could you set in order to use procmon to glean information?
I will set PID is 1072 filter to glean information.
5) What are the malware’s host-based indicators?
By default, this malware installs as a service called "IPRIP" with the description: "Depends INA+, Collects and stores network configuration and location information, and notifies applications when this information changes.". So this kind of registry write is a host-based indicator indeed. As I mentioned earlier this malware is able to have different names than IPRIP so every name displayed as a service from the SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost\netsvcs registry key is a host-based indicator. In addition to this, the malware writes itself into \HKLM\ControlSet001\Services\ for persistence. To be able to detect this malware on any machine we can use Process Explorer and search for Lab03-02.dll. The process that loaded this DLL into memory is the malware's host-based indicator.
6) Are there any useful network-based signatures for this malware?
To gain information about the networking activity of the malware I set the ApateDNS with redirection to the address IP of my fake network Linux machine. On the Linux machine, there was INetSim running that created a fake network. Obviously, there was also Wireshark launched on the Windows machine to capture packets sent by the malware.
Wireshark tells us that the malware sent GET (HTTP) request to the domain practicalmalwareanalysis.com to get a serve.html file.
ApateDNS detected that there is a contact between the malware and practicalmalwareanalysis.com domain.
These two pieces of information are strong network-based signatures for this malware.
Analyze the malware found in the file Lab03-02.dll using basic dynamic analysis tools.
Questions:
1. How can you get this malware to install itself?
2. How would you get this malware to run after installation?
3. How can you find the process under which this malware is running?
4. Which filters could you set in order to use procmon to glean information?
5. What are the malware’s host-based indicators?
6. Are there any useful network-based signatures for this malware?
My answers:
1) How can you get this malware to install itself?
This malware is the DLL file so we have to run it manually since OS doesn't know how to launch it automatically. rundll32.exe was created to run DLLs and I'm going to use it to be able to do basic dynamic analysis on Lab03-02.dll file. The executable which can run DLL files actually only calls the indicated method within a DLL. Therefore when we want to install this malware we have to find the appropriate function to call. I'll use pestudio to examine Exports of the Lab03-02.dll file.
Exports:
ServiceMain and UninstallService functions indicate that this kind of malware is a service. To confirm this supposition we can look for imports and check if this dll uses other methods responsible for handle services.
And the Import Table gives us very interesting information:
Methods marked with a red rectangle are responsible for handle services indeed. Now we are sure that Lab03-02.dll installs itself as a service. Within a blue rectangle, there are functions that are here probably due to saving a service into the registry. Orange rectangle marked methods that indicate the behavior of the malware. Lab03-02.dll probably delivers the next module of the malware through HTTP protocol and this DLL might be a downloader.
So now when we know that the service is probably saved within the registry we might be able to get the name of this service from the registry and then run it.
Before installation, it's worth launching several tools to get as much information as possible from our basic dynamic analysis.
1. Run Process Explorer to examine processes running on the system
2. Start Wireshark to capture packets and analyze network traffic between malware and the server
3. Create a fake network using the Linux machine with INetSim and ApateDNS on the Windows machine to redirect malware into the fake HTTP server running on the Linux machine.
4. Take a snapshot of the registry using Regshot and after running malware take a second snapshot, then compare two snapshots. As a result, we will probably get the name of the service written into the registry.
To install this malware we should call Install or installA function. Let's try the first option:
There were no errors so it looks like the service is installed successfully using Install method.
2) How would you get this malware to run after installation?
After the successful installation of the service, there is probably the new key added to the registry with the name of the service. So the first thing to do is to take the second snapshot of the registry using Regshot and compare it with the first one. As a result of this, we can get the name of the service and if we have the name of the service we can basically run it.
IPRIP is probably the name of the installed service after running Lab03-02.dll. Let's confirm it by looking deeper into the information provided by Regshot. If you take a look at Values added section of the text file provided by Regshot you would see this exact line among others:
Obviously in your case folders might be different but the fact is this write in the registry means that the IPRIP service is created by Lab03-02.dll indeed.
So to run this malware after installation I simply used this command:
net start "IPRIP"
What is interesting, "IPRIP" isn't the only possible name for this service. If we examine strings carefully we should see that in the bunch of trash there is something very useful for us ->
This line of characters means that the list of possible names for the service is in SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost\netsvcs registry key. If you take a look at this key you will see that the other possible names for this service are:
- 6to4
- AppMgmt
- AudioSrv
- CryptSvc
- DMServer
- DHCP
...
- and of course IPRIP
All of these names can be used to indicate the malware on infected machines. Furthermore, now we can suppose that the function installA <name to specify> can install the malware with any name from the netsvcs list.
3) How can you find the process under which this malware is running?
The best way to find the process under which this malware is running is to use Find -> Handle or DLL and type Lab03-02.dll. After doing this in Process Explorer this tool will give us the malware's process.
Now we know that the process under which this malware is running is svchost.exe with PID 1072.
4) Which filters could you set in order to use procmon to glean information?
I will set PID is 1072 filter to glean information.
5) What are the malware’s host-based indicators?
By default, this malware installs as a service called "IPRIP" with the description: "Depends INA+, Collects and stores network configuration and location information, and notifies applications when this information changes.". So this kind of registry write is a host-based indicator indeed. As I mentioned earlier this malware is able to have different names than IPRIP so every name displayed as a service from the SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost\netsvcs registry key is a host-based indicator. In addition to this, the malware writes itself into \HKLM\ControlSet001\Services\ for persistence. To be able to detect this malware on any machine we can use Process Explorer and search for Lab03-02.dll. The process that loaded this DLL into memory is the malware's host-based indicator.
6) Are there any useful network-based signatures for this malware?
To gain information about the networking activity of the malware I set the ApateDNS with redirection to the address IP of my fake network Linux machine. On the Linux machine, there was INetSim running that created a fake network. Obviously, there was also Wireshark launched on the Windows machine to capture packets sent by the malware.
Wireshark tells us that the malware sent GET (HTTP) request to the domain practicalmalwareanalysis.com to get a serve.html file.
ApateDNS detected that there is a contact between the malware and practicalmalwareanalysis.com domain.
These two pieces of information are strong network-based signatures for this malware.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Lab 3-3
Execute the malware found in the file Lab03-03.exe while monitoring it using basic dynamic analysis tools in a safe environment.
Questions:
1. What do you notice when monitoring this malware with Process Explorer?
2. Can you identify any live memory modifications?
3. What are the malware’s host-based indicators?
4. What is the purpose of this program?
My answers:
As always to do the basic dynamic analysis we have to set the appropriate tools for this task. Here's what I'm going to do:
1. Launch the Process Monitor with the filter set to Process Name is Lab03-03.exe.
2. Run the Process Explorer to gain information about processes running on the system and to identify live memory modifications within the Lab03-03.exe file.
3. Launch Wireshark to capture packets sent by malware.
4. Set ApateDNS to redirect DNS requests done by malware to fake network services running on the Linux machine.
5. Take a snapshot of the registry using Regshot to be able to see changes within the registry after work done by malware.
1. What do you notice when monitoring this malware with Process Explorer?
I've looked at the Process Explorer output and I've seen that Lab03-03.exe had created svchost.exe process that was orphaned after Lab03-03.exe ended the execution. svchost.exe as an orphaned process is highly suspicious therefore I continued further analysis. I think that this rare situation was the result of process replacement done by the malware on svchost.exe actually.
2) Can you identify any live memory modifications?
Live memory modifications can be investigated using Process Explorer tool. By this very useful program, we can compare strings that were within the disk image of the svchost.exe with the live memory image of the svcshost.exe. When the difference will appear then we can be sure that process replacement has taken place. So let's have a look at string comparison between two images.
To be able to compare strings we have to open two windows of the newly created svchost.exe process. The first one: Properties -> Strings -> check the Disk option, the second one: Properties -> Strings -> check the Memory option.
Strings from the disk image of svchost.exe are different than from its memory so the malware did process replacement on svchost.exe indeed. From the marked strings in memory, we can suppose that this malicious program is a keylogger running in the background.
3) What are the malware’s host-based indicators?
One of the host-based indicators is the practicalmalwareanalysis.log file that probably collects the keystrokes typed by the victim. The next host-based indicator is the orphaned svchost.exe process.
4) What is the purpose of this program?
To confirm our earlier supposition that this malware is a keylogger, it's worth to create the text file and type some characters inside it. Process Monitor can give us an answer to our question by logging called syscalls.
To begin with, let's start capturing events and set the filter to Operation is WriteFile. Then it's time to create new text files and type something inside it.
After typing something into the text file WriteFile function call appears immediately in the list provided by Process Monitor. Now we can be sure that the analyzed file is a keylogger. Let's have a look at practicalmalwareanalysis.log file out of curiosity.
This log file collects each of the keystrokes done on the infected system and could be sent to the server own by the attacker.
Execute the malware found in the file Lab03-03.exe while monitoring it using basic dynamic analysis tools in a safe environment.
Questions:
1. What do you notice when monitoring this malware with Process Explorer?
2. Can you identify any live memory modifications?
3. What are the malware’s host-based indicators?
4. What is the purpose of this program?
My answers:
As always to do the basic dynamic analysis we have to set the appropriate tools for this task. Here's what I'm going to do:
1. Launch the Process Monitor with the filter set to Process Name is Lab03-03.exe.
2. Run the Process Explorer to gain information about processes running on the system and to identify live memory modifications within the Lab03-03.exe file.
3. Launch Wireshark to capture packets sent by malware.
4. Set ApateDNS to redirect DNS requests done by malware to fake network services running on the Linux machine.
5. Take a snapshot of the registry using Regshot to be able to see changes within the registry after work done by malware.
1. What do you notice when monitoring this malware with Process Explorer?
I've looked at the Process Explorer output and I've seen that Lab03-03.exe had created svchost.exe process that was orphaned after Lab03-03.exe ended the execution. svchost.exe as an orphaned process is highly suspicious therefore I continued further analysis. I think that this rare situation was the result of process replacement done by the malware on svchost.exe actually.
2) Can you identify any live memory modifications?
Live memory modifications can be investigated using Process Explorer tool. By this very useful program, we can compare strings that were within the disk image of the svchost.exe with the live memory image of the svcshost.exe. When the difference will appear then we can be sure that process replacement has taken place. So let's have a look at string comparison between two images.
To be able to compare strings we have to open two windows of the newly created svchost.exe process. The first one: Properties -> Strings -> check the Disk option, the second one: Properties -> Strings -> check the Memory option.
Strings from the disk image of svchost.exe are different than from its memory so the malware did process replacement on svchost.exe indeed. From the marked strings in memory, we can suppose that this malicious program is a keylogger running in the background.
3) What are the malware’s host-based indicators?
One of the host-based indicators is the practicalmalwareanalysis.log file that probably collects the keystrokes typed by the victim. The next host-based indicator is the orphaned svchost.exe process.
4) What is the purpose of this program?
To confirm our earlier supposition that this malware is a keylogger, it's worth to create the text file and type some characters inside it. Process Monitor can give us an answer to our question by logging called syscalls.
To begin with, let's start capturing events and set the filter to Operation is WriteFile. Then it's time to create new text files and type something inside it.
After typing something into the text file WriteFile function call appears immediately in the list provided by Process Monitor. Now we can be sure that the analyzed file is a keylogger. Let's have a look at practicalmalwareanalysis.log file out of curiosity.
This log file collects each of the keystrokes done on the infected system and could be sent to the server own by the attacker.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Lab 3-4
Analyze the malware found in the file Lab03-04.exe using basic dynamic analysis tools. (This program is analyzed further in the Chapter 9 labs.)
Questions:
1. What happens when you run this file?
2. What is causing the roadblock in dynamic analysis?
3. Are there other ways to run this program?
My answers:
Obviously, we should launch appropriate tools before doing analysis include Process Monitor, Process Explorer, Regshot (to be able to check for host-based indicators), Wireshark, ApateDNS, and INetSim on the fake network machine. (to be able to check for network-based indicators)
1. What happens when you run this file?
After double-clicking this program just deletes itself.
2. What is causing the roadblock in dynamic analysis?
In the process of deletion, it's possible to see the console for the moment. This it can mean that the subsystem of this program is Console, therefore, missed console arguments can cause the roadblock in dynamic analysis. Let's see if I'm right about the subsystem:
Yeah, the subsystem of this executable is "console" indeed.
3. Are there other ways to run this program?
I was trying to find console arguments in the list of the strings within the Lab03-04.exe but nothing was interesting enough. The list of significant (in my opinion) strings is here:
- SOFTWARE\Microsoft \XPS
- GET
- NOTHING
- DOWNLOAD
- UPLOAD
- SLEEP
- /c del
- http://www.practicalmalwareanalysis.com
- HTTP/1.0\r\n\r\n
- >> NUL
Using this list we can suppose that this malware might be the backdoor since it can communicate with practicalmalwareanalysis.com domain through HTTP protocol and probably downloads and uploads files from there. We don't have any console arguments in our hands so the only thing we can do to run this file is to simply execute it within the cmd.exe. Before this, we should launch all of the basic dynamic analysis tools to gain as much information as we can.
Process Monitor filter should be set like this: Process Name is Lab03-04.exe.
To my surprise, after executing this file in the console without any argument everything works fine. As you can see Process Monitor provided a quite long list of called syscalls by the executable:
From the list of 1743 syscalls is hard to tell what this malware is really doing. Furthermore, it can be obfuscated. The interesting thing is that I have not found any networking action done by this malware. In my opinion, just the basic dynamic analysis is not enough in this case and further analysis process must take place. The book said that this executable is analyzed further in Chapter 9 thus I leave it as it is and when I'm ready I will analyze it deeper.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
And that's all for the basic dynamic analysis tasks from the book.
Thank you for reading.
Cheers!
Analyze the malware found in the file Lab03-04.exe using basic dynamic analysis tools. (This program is analyzed further in the Chapter 9 labs.)
Questions:
1. What happens when you run this file?
2. What is causing the roadblock in dynamic analysis?
3. Are there other ways to run this program?
My answers:
Obviously, we should launch appropriate tools before doing analysis include Process Monitor, Process Explorer, Regshot (to be able to check for host-based indicators), Wireshark, ApateDNS, and INetSim on the fake network machine. (to be able to check for network-based indicators)
1. What happens when you run this file?
After double-clicking this program just deletes itself.
2. What is causing the roadblock in dynamic analysis?
In the process of deletion, it's possible to see the console for the moment. This it can mean that the subsystem of this program is Console, therefore, missed console arguments can cause the roadblock in dynamic analysis. Let's see if I'm right about the subsystem:
Yeah, the subsystem of this executable is "console" indeed.
3. Are there other ways to run this program?
I was trying to find console arguments in the list of the strings within the Lab03-04.exe but nothing was interesting enough. The list of significant (in my opinion) strings is here:
- SOFTWARE\Microsoft \XPS
- GET
- NOTHING
- DOWNLOAD
- UPLOAD
- SLEEP
- /c del
- http://www.practicalmalwareanalysis.com
- HTTP/1.0\r\n\r\n
- >> NUL
Using this list we can suppose that this malware might be the backdoor since it can communicate with practicalmalwareanalysis.com domain through HTTP protocol and probably downloads and uploads files from there. We don't have any console arguments in our hands so the only thing we can do to run this file is to simply execute it within the cmd.exe. Before this, we should launch all of the basic dynamic analysis tools to gain as much information as we can.
Process Monitor filter should be set like this: Process Name is Lab03-04.exe.
To my surprise, after executing this file in the console without any argument everything works fine. As you can see Process Monitor provided a quite long list of called syscalls by the executable:
From the list of 1743 syscalls is hard to tell what this malware is really doing. Furthermore, it can be obfuscated. The interesting thing is that I have not found any networking action done by this malware. In my opinion, just the basic dynamic analysis is not enough in this case and further analysis process must take place. The book said that this executable is analyzed further in Chapter 9 thus I leave it as it is and when I'm ready I will analyze it deeper.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
And that's all for the basic dynamic analysis tasks from the book.
Thank you for reading.
Cheers!





























Comments
Post a Comment